Malicious emails have gotten good, like really good. They can make any email look authentic, but is it? Today we are going to follow a trail of malicious emails and discover some tactics attackers use.
Spoofing and Phishing Email
Before getting into a specific example let’s start with the basics. When someone spoofs an email they are creating a fake unofficial email and attaching an official name to that email. In the body of the email is typically a phishing attack. A phishing attack is when someone tricks you into revealing personal information like a username and password.
That may sound confusing so lets look at an example.
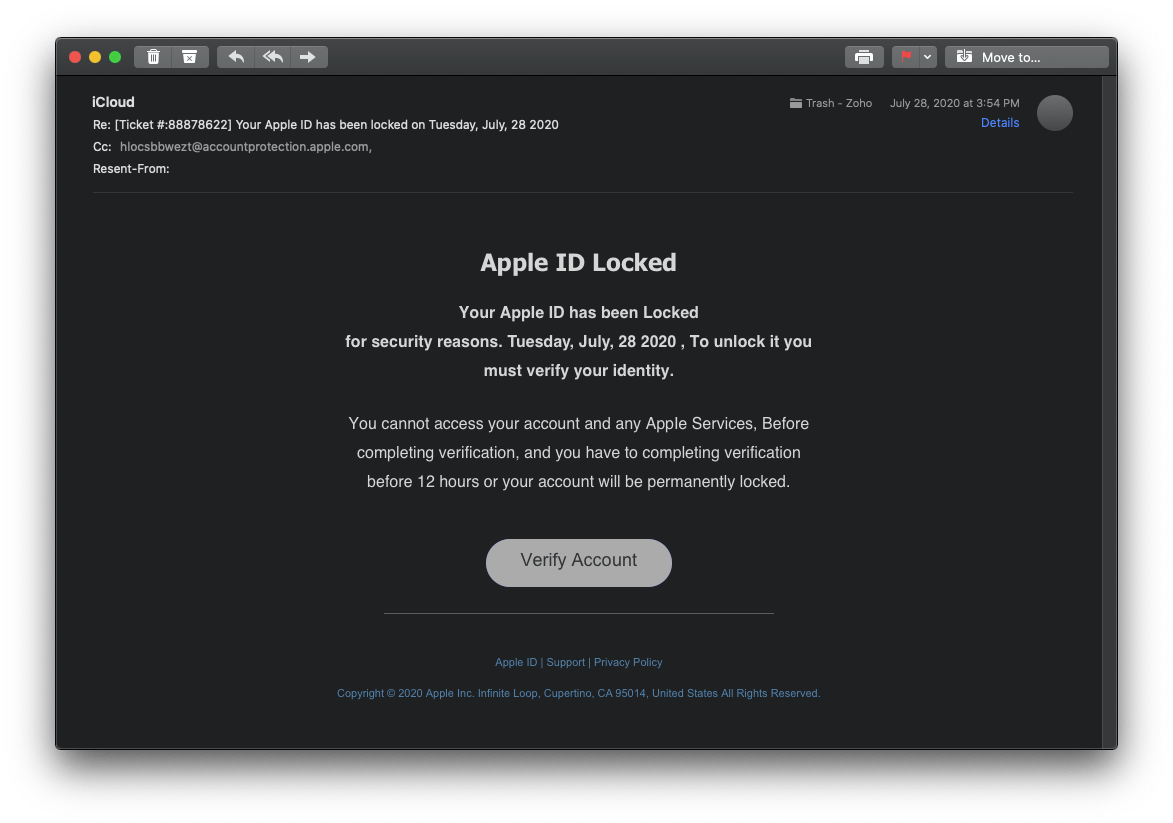
Here is an email from iCloud giving me a ticket number and telling me that my Apple ID has been locked. Is this email really from Apple? No. To prove this let’s examine the email in Apple’s native Mail app.
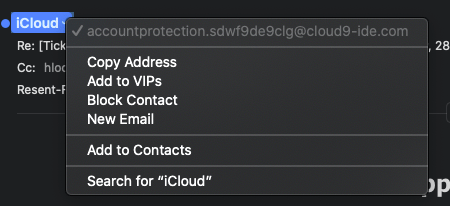
When I hover over the sender’s name “iCloud” and click the down arrow a menu will appear where you can see “iCloud”‘s email address. This email came from accountprotection.sdwf9de9clg@cloud9-ide.com. You can tell where this email came from by looking to the right of the at symbol (@). In this case, this email is coming from cloud9.ide.com which is obviously not Apple.com. Therefore it’s not an official email from Apple.
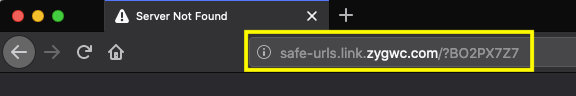
However, if we skip over the fact that this email didn’t come from Apple lets look at the “Verify Account” button at the bottom of the email. Clicking the button will open the link in your default browser. The site address is safe-urls.link.zygwc.com/?BO2PX7Z7. If this site worked it would most likely ask for me to enter my Apple ID, which I would never do. If we look at the domain zygwc.com we can once again tell that we are not on Apple.com. Once again proving that not only is this email spoofing Apple but it is also an attempted phishing attack to get my AppleID.
On the topic of emails from “Apple”, Apple will never send you an email with a Microsoft Word document attached. In general, never open Word documents from unknown senders. That document could hold malicious code that could give an attacker access to your computer.
Next Level
Let’s see what happens when attackers take it to the next level.
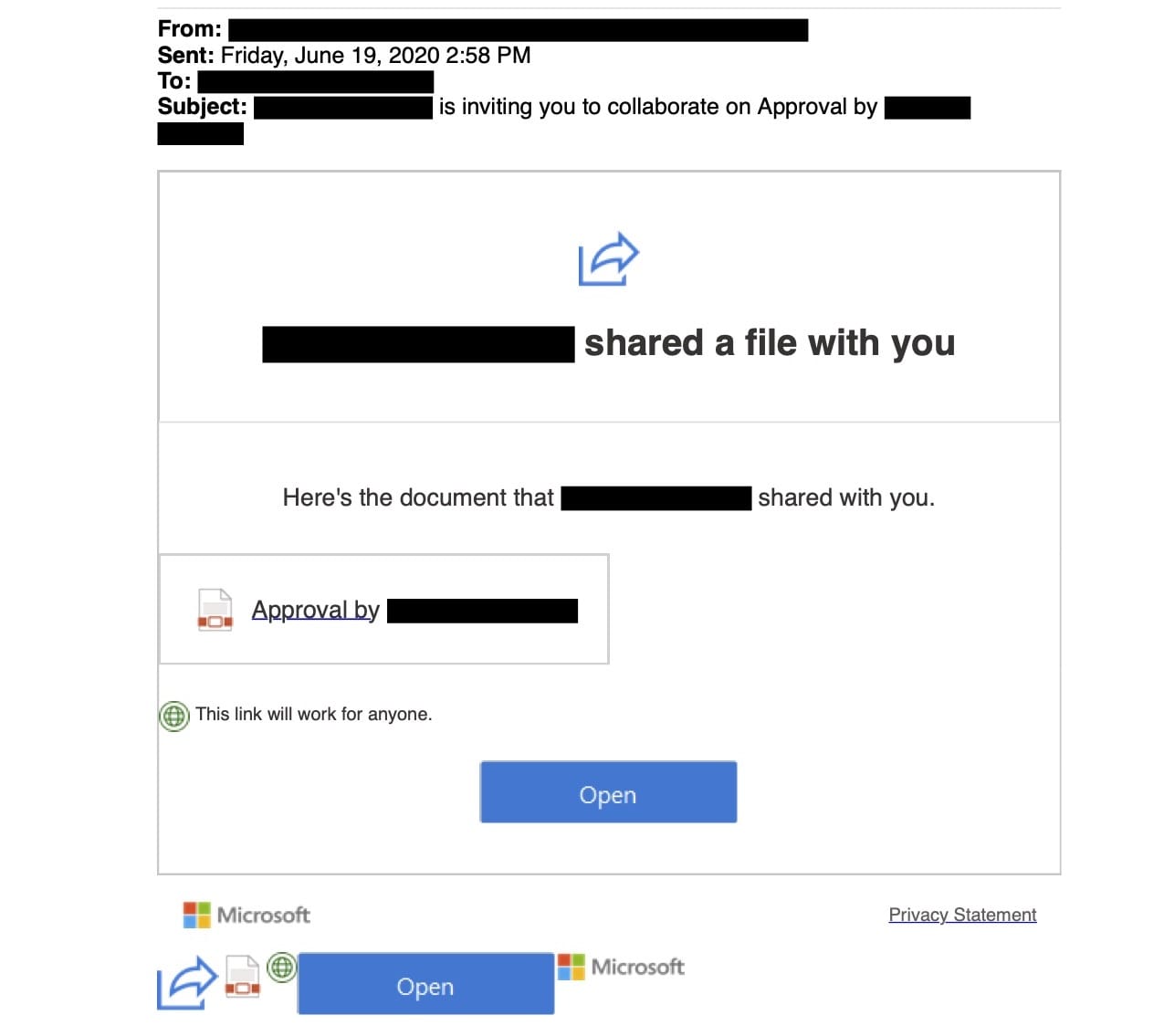
This is an invite to a PDF document via Microsoft Sharepoint. Sharepoint is Microsoft’s online collaboration software for business. Believe it or not, this is a completely authentic Microsoft Sharepoint email. The email, which I have hidden for privacy reasons, is a real email that belongs to the sender and has not been spoofed. When I click “Open” the link opens in by default browser taking me to a PDF shared via Microsoft Sharepoint. Once again everything here is authentic. What’s in the PDF is where things get fishy.
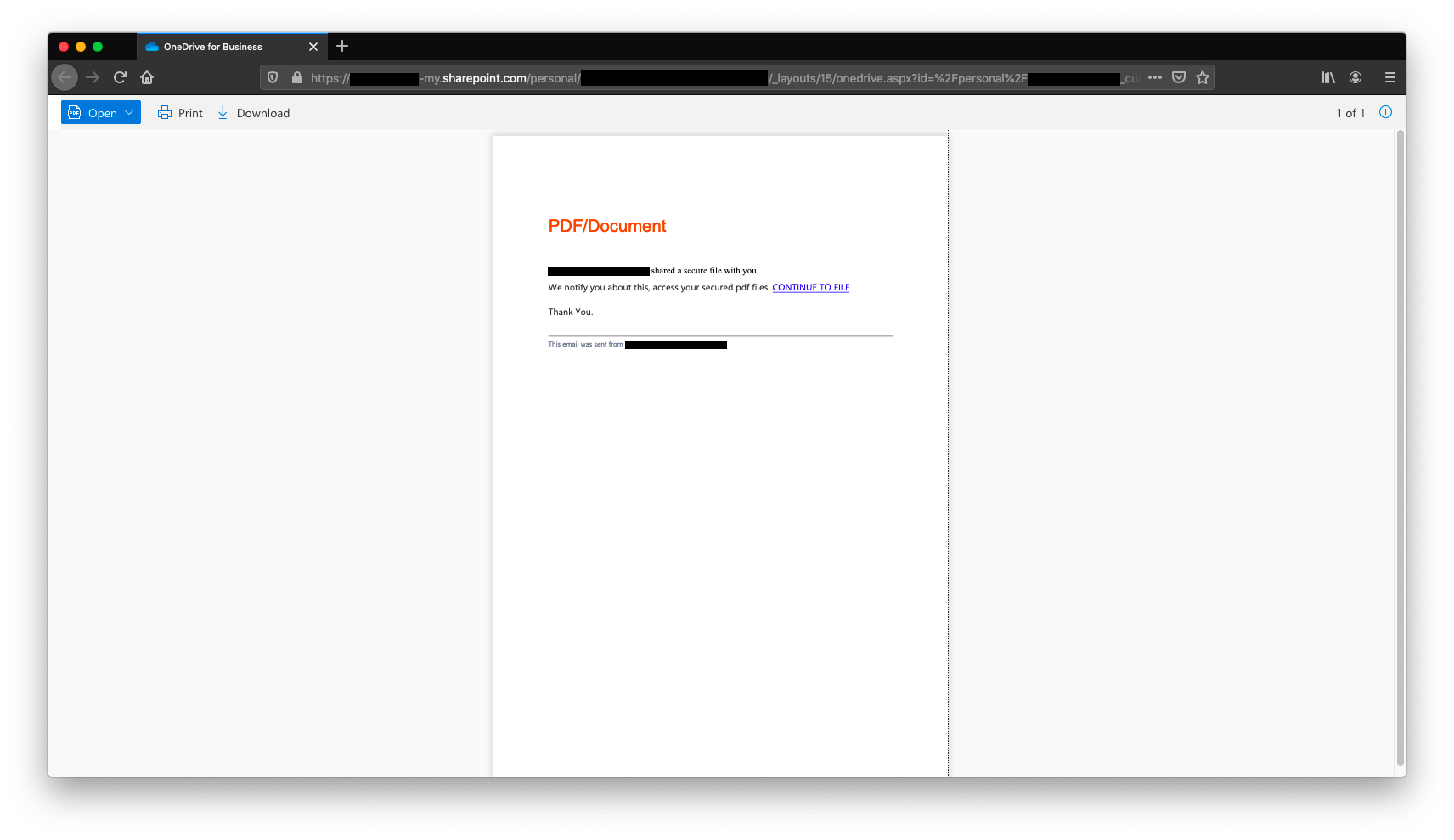
The PDF tells me that I have to click the “CONTINUE TO FILE” link to access the “files”. After clicking the link I get a warning from my browser telling me I’m entering an unsafe site, which is a big red flag. But to see where it goes I’m going to ignore the warning. However, I do not recommend you do the same. If your browser tells you your entering an unsafe site TURN AWAY.
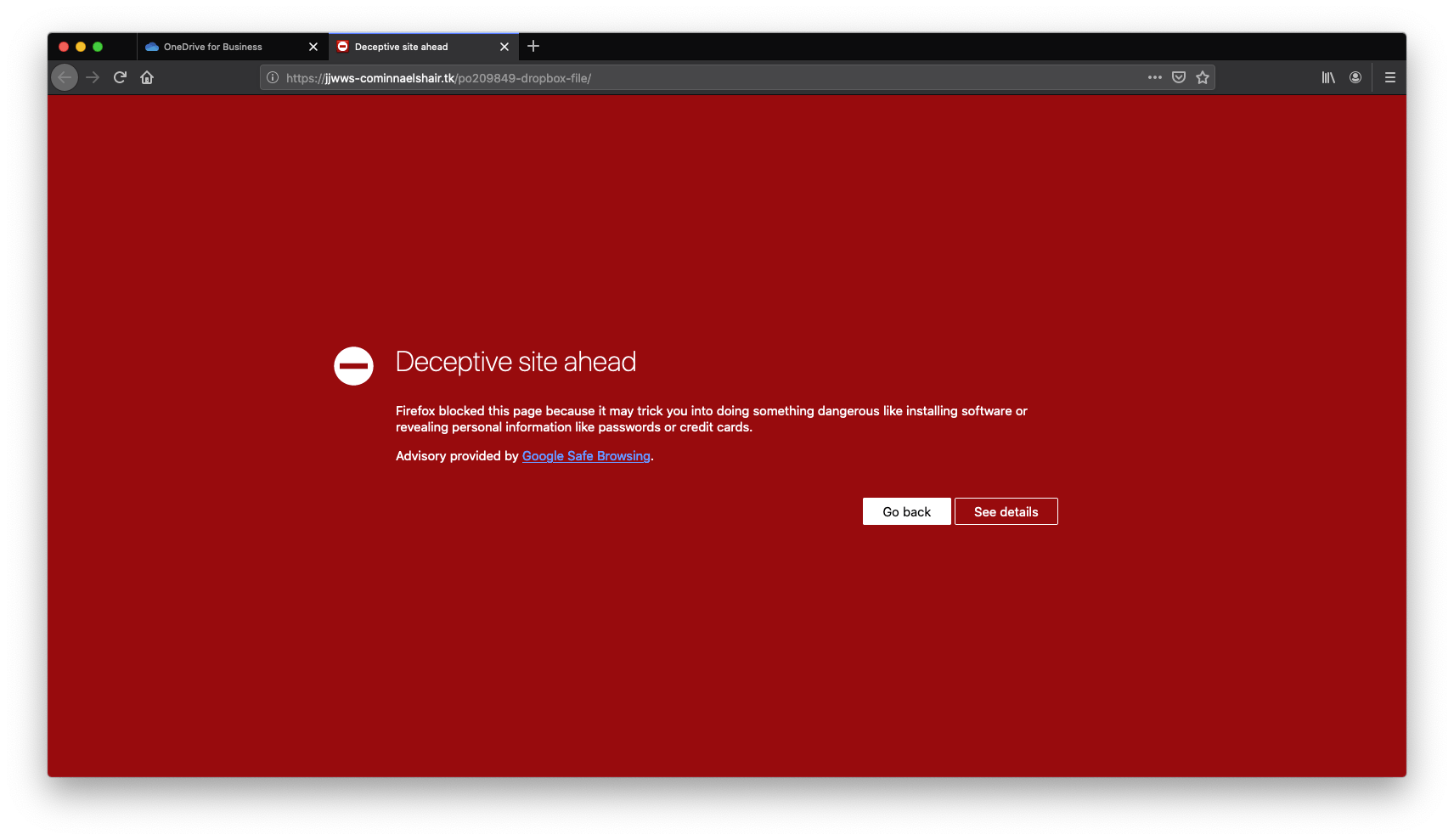
Now I’m taken to a site with a URL of https://jjwws-cominnaelshair.tk/po209849-dropbox-file. Unfortunately, this site no longer opens. Previously, when it did, it would ask me to sign in with my Dropbox account to access the files. This is where I call it quits.
Now that we make it to the end of the chain, and way further than I would recommend anyone going, let’s look into this “Dropbox” sign-in page. To do this we are going to examine the domain. The .tk tells us that the site is registered to a New Zealand territory. When I go to their website, as if to purchase my own .tk domain, I learn that you can get a .tk address for free. Because it’s free it’s perfect for attackers. The Anti Phishing Working Group has logged that about 20% of .tk sites are used for phishing attacks like seen here.
As you can see email attackers go to great lengths in an attempt to collect your private information. With this I hope you can now know what to look out for in spoofing and phishing attacks.
Additional Resources
- Wikipedia: Email Spoofing
- Wikipedia: Phishing
- Apple Support: Recognize and avoid phishing messages, phony support calls, and other scams
Subscribe: Apple Podcasts | Google Podcasts | Spotify | Amazon Music | Android | Pandora | Blubrry | Email | TuneIn | RSS | More

